What is phishing in cryptocurrency?
Phishing is a type of cryptocurrency scam that involves tricking victims into giving up their private keys or personal information. The attacker typically masquerades as a legitimate entity or person to gain the trust of the victim. Once the victim has been scammed, the attacker then uses their information to steal their cryptocurrency funds.
Phishing scams are becoming increasingly common as cybercriminals and cyber attacks grow more sophisticated. Many of these target wallets, cryptocurrency exchanges and initial coin offerings. Thus, crypto users must be aware of how they work to protect themselves and their funds.
In this article, we'll discuss how phishing scams work, ways to recognize them and tips on how to avoid phishing attacks.
How does a phishing attack work?
A phishing attack usually starts with an attacker sending out a mass email or message to potential victims. It will often look like it is from a legitimate source, such as a wallet or cryptocurrency exchange.
The message almost always contains a link that leads to a fake website that looks identical to the real one. Once the victim clicks on the link and inputs their login information, the attacker (mis)uses it to access their account.
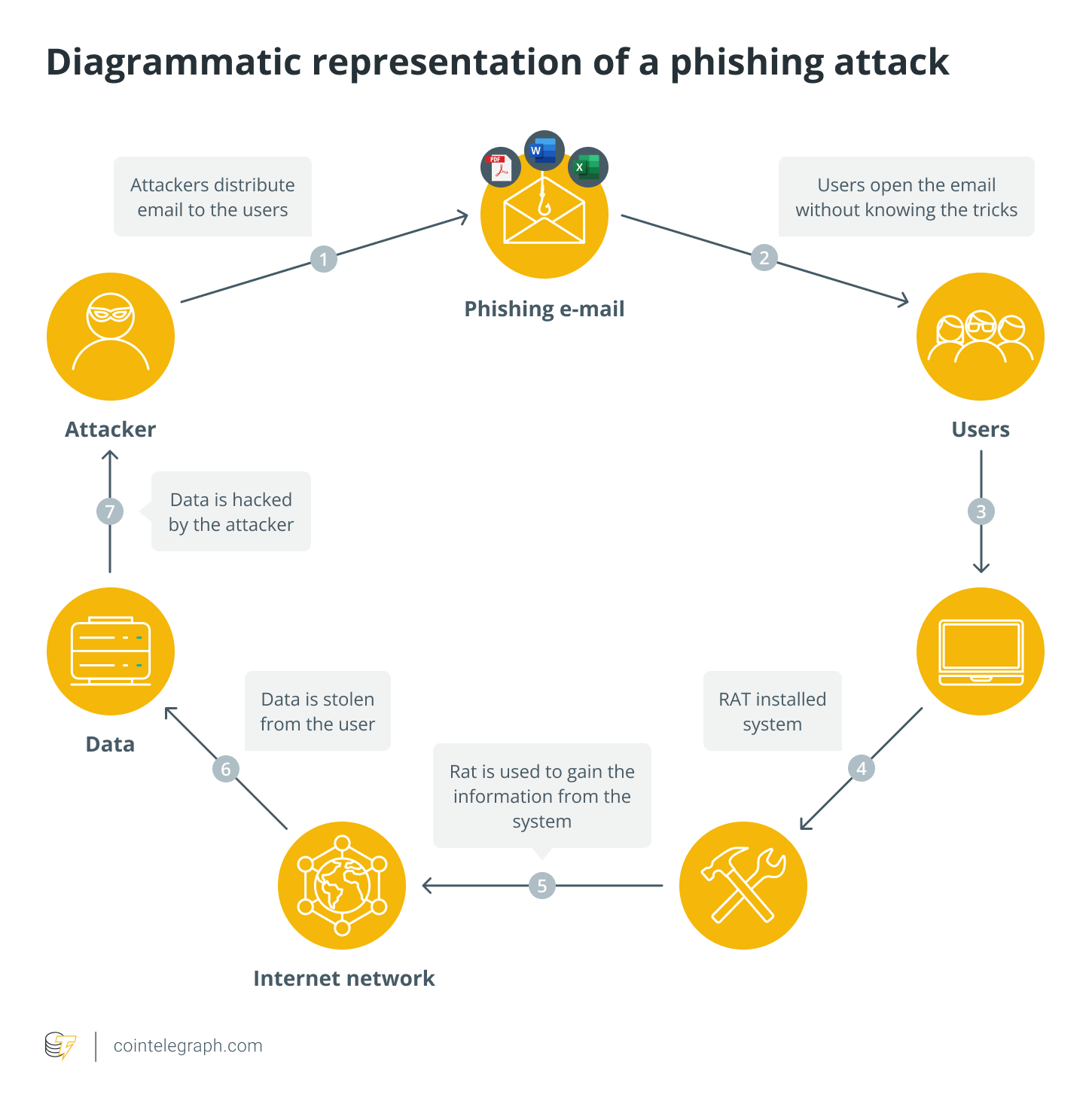
Phishing attacks prompt a target into action by appealing to their sense of urgency or fear. For example, a message may claim a problem with the victim's account and that they must log in immediately to fix it. Others try to entice victims by offering a fake bounty or airdrop.
Some attackers even feign concern by alerting account owners of "suspicious activity" to get them to input their login credentials on a fake website.
Ways to recognize a phishing email?
Unfortunately, phishing emails can be quite difficult to spot. Most phishers go to great lengths to make their emails and websites look legitimate. But, here are some red flags to look out for:
Copycatting
Copycatting involves duplicating the distinctive content of an organization, such as specific text, typefaces, logos or color schemes on the genuine website.
The best way to avoid copycat phishing is to familiarize yourself with the branding of the organizations with which you deal. That way, you will be more likely to catch an imposter.
Spelling or grammar errors
Phishing emails often contain mistakes in spelling or grammar. Phishers are usually in a hurry to get their message out and don't take time to proofread. In some cases, they are not adept in the language they are using. If you see an email with obvious errors, it is most likely a phishing attempt.
Misleading links
Another way to phish someone is by including a link in the email that appears to go to the legitimate website but instead takes you to a fake site. A common approach to phishing attacks is using shortened uniform resource locators (URLs) or embedded links that disguise the true destination site.
For example, the displayed anchor text for a hyperlink may differ significantly from the true link URL. To visually mimic an authentic link destination, the phisher utilizes small errors such as substituting a lowercase "i" with an uppercase "I."
Using a public email instead of a corporate one
Attackers often use a public email account because it is easier to create a fake email with a public domain than a corporate one. Hence, an official-sounding email that ends in "@gmail.com" instead of "@companyname.com" should immediately arouse suspicion.
Content misalignment
Another way to spot a phishing email is by looking for content misalignment. When phishers mimic a legitimate email, they don't always get the details right. It may have a different tone or style than what you regularly get from a particular company.
In some instances, a mismatch between messages and embedded images could signal a phishing attempt. For example, the email may say "click here to login," but the button says "click here to sign up."
Common crypto phishing attacks
A few types of phishing attacks are particularly common in the cryptocurrency space:
Spear phishing attack
Spear phishing is a targeted attack aimed at a specific individual or organization. Here, the phisher has some prior knowledge about their target and will use this to tailor the phishing email so it looks legitimate. For example, the attacker will spoof an email from a person or organization familiar to the victim. A malicious link disguised as an innocent one is then added.
Whaling attack
A whaling attack is a specific type of spear phishing attack targeting high-profile individuals within an organization, such as CEOs. It's particularly dangerous due to its potentially wider reach than a regular spear phishing attack. For instance, if a CEO falls for it and clicks on a malicious link, the attacker could gain access to the company's entire network.
Clone phishing attack
This attack happens when the phisher creates a replica of a legitimate email that has been sent to the target in the past.
The attacker replaces the original attachment or link with a malicious one and sends it to the victim. Since the email looks identical to one previously received by the victim, they are more likely to click on the link out of habit or familiarity.
Pharming attack
In this type of phishing attack, a victim is redirected to a fake website, even if they enter the correct URL.
This is usually done by infecting the DNS server, which is responsible for converting URLs into IP addresses, with malicious code. The code will then redirect victims to the attacker's fake website when they try to visit a legitimate website.
Pharming attacks are particularly dangerous because they can be very difficult to spot. A victim may enter the correct URL for their bank's website but still land on a fake website that looks identical to the real one.
Evil twin attack
An evil twin phishing attack targets public Wi-Fi networks. Here's how attackers do it: They will set up a fake Wi-Fi network using the same name as a legitimate network. When victims connect to the network, they will be prompted to enter their login credentials, which the phishers can then use to gain access to their accounts.
Voice phishing attack
Also known as vishing, this type of phishing uses voice calls or voicemails instead of emails. It usually happens on voice-based media, such as voice-over IP or conventional residential phone service.
In a voice phishing attack, the attacker spoofs the caller ID to make it appear as if they are calling from a legitimate organization, such as a bank. Vishing fraudsters frequently employ speech synthesis software to leave voicemails warning potential victims of fraudulent activity in their bank or credit accounts.
SMS phishing attack
SMS phishing, sometimes called smishing, uses text messages instead of emails. Smishing attackers send seemingly legitimate company text messages to their victims. When a victim clicks on the link within the SMS, they will be prompted to enter their login credentials, which the attacker uses to access their account.
DNS hijacking
Domain Name System (DNS) hijacking redirects victims to a fake website by changing the DNS entries for a legitimate website. To execute the attack, a phisher replaces the DNS entries, so they point to a different IP address. When victims try to visit the legitimate website, they will be redirected to the attacker's fake website instead.
The attack is then carried out by loading malware on people's computers, taking control of routers, or interfering with DNS communications.
Phishing bots
Phishing bots are computer programs that automate phishing attacks. They can be used to send out mass phishing emails, create fake websites, and host those sites on servers. Such bots could also automatically collect victims' login credentials and other sensitive information.
These programs are often applied in conjunction with other types of attacks, such as denial-of-service attacks and spamming.
Fake browser extensions
These extensions are malicious plugins designed to resemble legitimate ones. They are often used to steal sensitive information, such as login credentials and credit card numbers. In addition, they can redirect victims to fake websites, inject malware into their computers, or display unwanted advertisements.
Fake browser extensions are usually distributed through phishing emails or malicious websites. When installed, they can be difficult to remove. The extensions are essentially phishing for private information such as mnemonic phrases, private keys, and Keystore files.
Ice phishing
In this form of phishing, the attacker will send the victim a fake transaction that appears to be from a legitimate source. The transaction will require the victim to sign it with their private key.
In other words, the victim is tricked into signing a transaction that transfers authority over their tokens to the fraudster. If the victim proceeds, they will unknowingly have transferred ownership of their tokens to the attacker.
Crypto-malware attack
A crypto-malware attack is a type of malware that encrypts the victim's files and demands a ransom to decrypt them. It can be spread through phishing emails, malicious websites or fake browser extensions.
Once installed on the victim's computer, the malware will encrypt their files and display the ransom message on their screen.
How to avoid a crypto phishing attack?
Below are some quick tips you can follow to avoid a crypto phishing attack:
Be cautious of emails, especially if they contain attachments or links. If you're unsure about an email, contact the sender directly to confirm its authenticity.
Don't click on links or download attachments from sources you don't trust.
Keep your operating system and software up to date.
Use strong passwords and never reuse passwords across different accounts.
Enable two-factor authentication when available.
Don't give out personal information, such as your wallet address or private keys, to anyone.
Use a reputable cryptocurrency exchange and wallet.
Be cautious of websites that look suspicious or too good to be true. When unsure, do a web search to see if others have reported it as being fake.
Don't download browser extensions from untrustworthy sources.
Use a VPN when connecting to the internet, especially if you're using public Wi-Fi.
Disclaimer : The above empty space does not represent the position of this platform. If the content of the article is not logical or has irregularities, please submit feedback and we will delete or correct it, thank you!